
Blog
Privacy and Environmental, Social and Corporate Governance (ESG)
What is ESG? ESG, or Environmental, Social and Corporate Governance, is the evaluation of a company’s commitment to improving environmental and social factors and the governance part, reporting on them…

Privacy Kitchen
Top 4 Brexit Impacts on your GRPR Program
In Part 1 of our series on Brexit, we saw that Brexit definitely did not kill GDPR. In fact, it split GDPR into two: the UK GDPR and the EU…
Privacy Kitchen
10 Steps to GDPR Compliance
10 Steps to GDPR Compliance Whether you’re a beginner with GDPR or you’re quite advanced and just wanting a sanity check, we’re going to give you 10 Steps to GDPR…
Blog
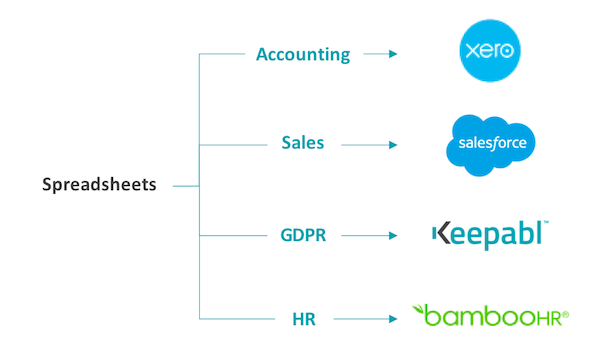
GDPR + SaaS = Happy Days
Our experience is that, after the last 18 months working on spreadsheets to manage GDPR, many organisations are now looking for SaaS to bring its many benefits to ongoing GDPR…

Blog Downloads
Compliance SaaS for MSPs – TubbTalk #56
All MSPs wanted to know about GDPR but were afraid (or just didn’t want) to ask! Join MSP thought leader and IT services consultant Richard Tubb, as he interviews our…

Blog
How MSPs can compete with Free
CompTIA’s unconference session, CompTIA UK Community meetup, Bristol, June 2019. The ‘unconference’ session is always a highlight of CompTIA Community meetups, and Bristol 2019 was no different. So much great…

Case Studies
ADBA Recommends Keepabl to Members
The UK Anaerobic Digestion & Bioresources Association chooses Keepabl to manage its own Privacy Governance, and recommends Keepabl to its members. The ADBA represents its members on policy matters and…
Blog
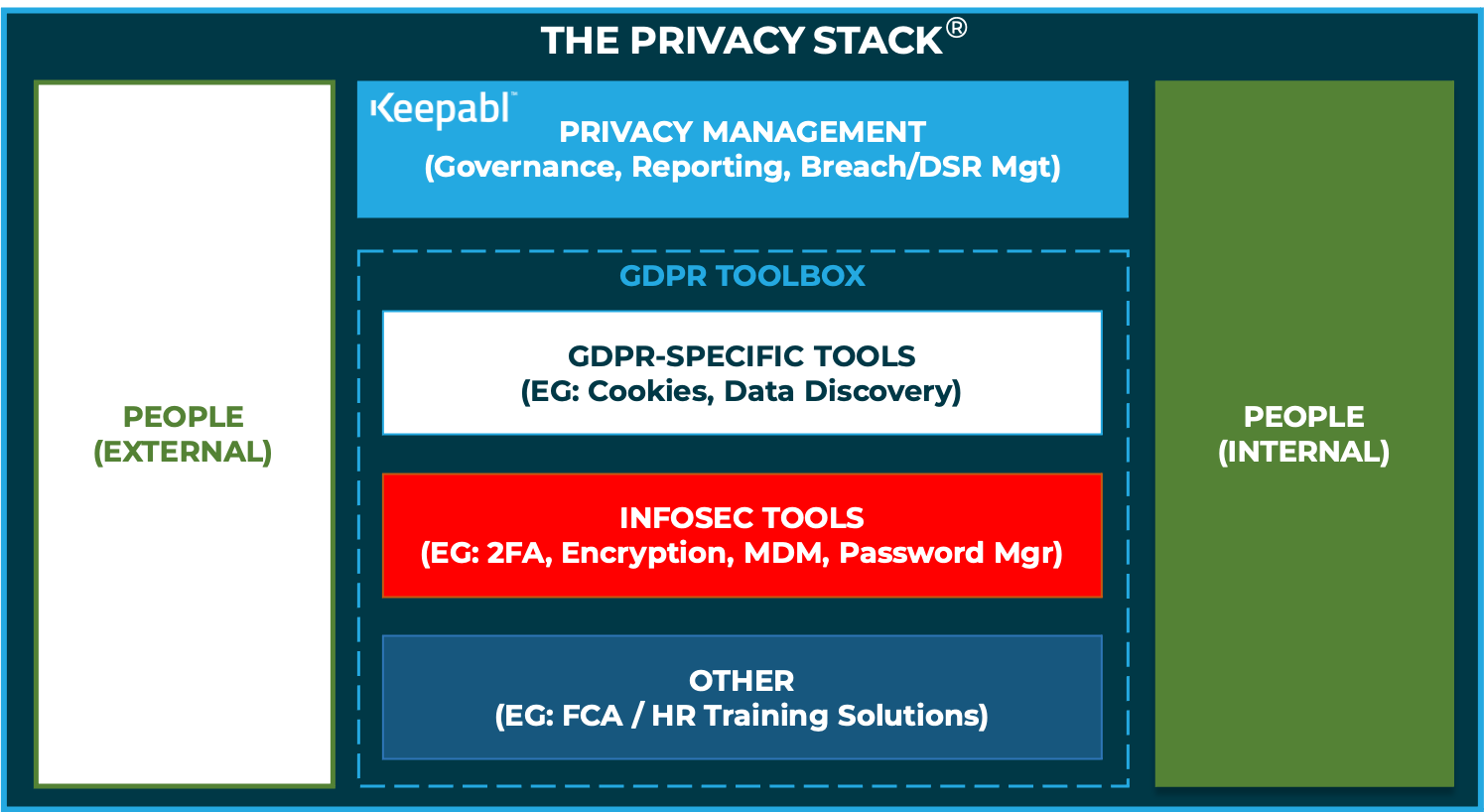
Introducing Keepabl's PRIVACY STACK
The Privacy Stack Here at Keepabl, we often say that the Privacy sector, kickstarted into life by GDPR in 2018, is 30 years behind Security as a practice and industry. …
Blog
Cordium & Keepabl: Benchmark GDPR regulatory readiness
Our latest Cordium Insights webinar outlines: best practices for assessing data processing, storage, and protection policies, tips for identifying and remediating control gaps and weakness and on how to develop…

